中国安全网 3月14日报道,McAfee称Vista的粘滞键(StickyKeys)可能被误用。McAfee说微软的Vista系统导致粘滞键不可避免地存在缺陷。
据Internetnews报道,本周一McAfee公司的一项研究报告指出,微软专门为有缺陷人士设计的一项简化操作的功能——粘滞键在Vista系统中可能会被误用。
所谓粘滞键专为同时按下两个或多个键有困难的人而设计的,当快捷方式需要组合键时,例如 CTRL+P,粘滞键可以使您一次只按一个键,而不是同时按两个键。
McAfee 公司一位名为Vinoo Thomas的研究者于本周一在其博客中指出,攻击者可以利用这项称之为粘滞键的功能来引诱使用者向Vista系统的电脑上下载盗版软件。
当一位Windows系统的使用者连续使用诸如Shift或Alt等切换键五次时粘滞键就会被调用。这使得该切换键的作用类似Shift和F1的联合使用功能,但是不需要同时使用两个键。
Thomas 写到一个攻击者可以通过执行一些命令替换用来调用粘滞键的名为sethc.exe的文件,就像Windows系统的命令功能一样。
这些后门脆弱性在Windows2000和WindowsXP系统中已经存在了。
虽然Vista系统仍然存在此项脆弱性,但是该后门程序能够被攻击者多大程度地利用还尚未明了,因为要首先登陆该台电脑才能对其上的粘滞键进行替换。
Thomas确信内部攻击者可以利用此项漏洞绕过终端工作站和服务器进行攻击。
微软负责人尚未就此事发表任何评论。
他同时写到,“个人用户可不需安装可获得性工具,这些都是默认安装的,可以避免此类虽然简单但是具有相当大潜在严重性的后门写入。另外,可以连续敲击shift键5次来观察是否有对话框在桌面上弹出。”为了避免问题的发生,可以撤消粘滞键,避免这类事件的发生的方法还是容易的,但是有潜在的隐患不可小看。
附:Vinoo Thomas原文《 Windows Vista Vulnerable to StickyKeys Backdoor》
Windows Vista Vulnerable to StickyKeys Backdoor
Monday March 12, 2007 at 8:11 am CST
Posted by Vinoo Thomas
Trackback
StickyKeys is an accessibility feature to aid handicapped users. It allows the user to press a modifier key, such as the Shift key, and have it remain active until another key is pressed. StickyKeys is activated by pressing the shift key or a modifier key five times in sequence and a beep is sounded. Sounds innocuous, right? Dead wrong!
Apparently, Windows Vista does not check the integrity of the file that launches StickyKeys “c:/windows/system32/sethc.exe” before executing it. Which means you could replace it with another executable and run it by depressing the shift key five times. A popular replacement is “cmd.exe.” After replacement, one could invoke this command prompt at the login prompt without the need to authenticate as shown in the below screenshot.
Invoking Sticky Keys
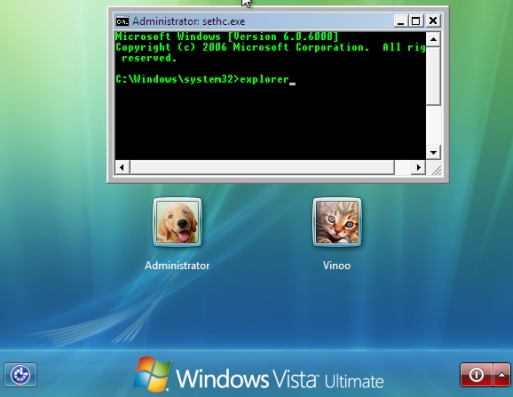
Once launched, it is possible to execute explorer.exe without authenticating and get a full desktop running under the credentials of the NT Authority\system account. And from this point on an attacker has full access to the system.
Launching desktop via Sticky Keys
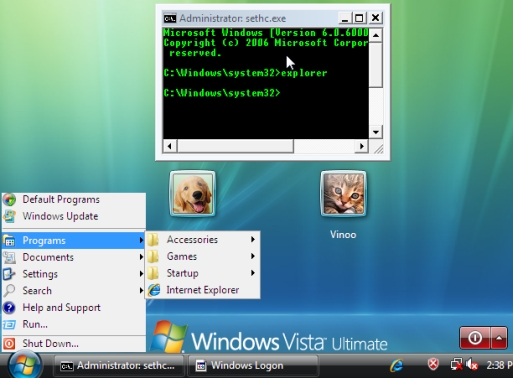
This legacy backdoor method is not something new–Win 2000 and XP are also vulnerable. Applying the latest Windows updates insures that “sethc.exe” is protected by Windows file protection. In Vista replacing system files is a more difficult because of Trusted Installer. However, running the following two commands nullifies this.
takeown /f c:\windows\system32\sethc.exe
cacls c:\windows\system32\sethc.exe /G administrator:F
To execute the above commands successfully, it requires an administrator to be logged in; but a determined attacker can always find workarounds to exploit this built-in backdoor. In fact once a command prompt is obtained via this method, we can use it to create a new user, add this user to the administrators group via the net command and then use this account to rightfully log in using the following commands.
net user USERNAME /add
net localgroup administrators USERNAME
One can always argue that an attacker actually needs access to the machine to be able to pull this off. Of all the unauthorized system access incidents that organizations reported last year, roughly 27% were by internal employees. And it is this threat from within (disgruntled or naughty employees) that poses the greatest computer security threat to organizations today.
Another alarming feature of this backdoor is that an attacker can use this method to bypass login on terminal servers and workstations with the remote desktop enabled. Since no third-party tools are being installed on the system and we are using Microsoft’s own files to achieve this, it will be difficult to detect for a typical administrator.
Perhaps one can uninstall the Accessibility Tools feature, which is installed by default to avoid this fairly simple, yet potentially serious built-in backdoor. And don’t forget to hit the shift key five times and see what pops up on your desktop.

